The yr 2024 is likely one of the greatest election years in historical past, with billions of individuals going to the polls across the globe. Though elections are thought-about protected, inside state affairs below worldwide regulation, election interference between nations has nonetheless risen. Specifically, cyber-enabled affect operations (CEIO) through social media—together with disinformation, misinformation or “pretend information”—have emerged as a singular risk that states have to counter.
Affect ops initially skyrocketed into public consciousness within the aftermath of Russian election interference within the 2016 U.S. presidential election. They haven’t since waned. Researchers, coverage makers and social media corporations have designed diverse approaches to counter these CEIOs. Nevertheless, that requires an understanding, typically lacking, of how these operations work within the first place.
Info, after all, has been used as a instrument of statecraft all through historical past. Solar Tzu proposed greater than 2,000 years in the past that the “supreme artwork of warfare” is to “subdue the enemy with out combating.” To that finish, info can affect, distract or persuade an adversary that it isn’t of their finest curiosity to struggle. Within the Nineteen Eighties, for instance, the Soviet Union initiated Operation Infektion/Operation Denver aimed toward spreading the lie that AIDS was manufactured within the U.S. With the emergence of our on-line world, such affect operations have expanded in scope, scale and pace.
On supporting science journalism
In case you’re having fun with this text, take into account supporting our award-winning journalism by subscribing. By buying a subscription you might be serving to to make sure the way forward for impactful tales in regards to the discoveries and concepts shaping our world immediately.
Visions of cybergeddon—together with catastrophic cyber incidents wreaking havoc on communications, the facility grid, waters provides and different very important infrastructure, leading to social collapse—have captured public creativeness and fueled a lot of the coverage discourse (together with references to a “cyber Pearl Harbor”).
But, cyber operations can take one other kind, focusing on the people behind the keyboards, relatively than machines via code manipulation. Such actions performed via our on-line world might be aimed toward altering an audiences’ considering and perceptions, with the purpose to in the end change their habits. Organizing political rallies in an adversary state could be an instance of mobilization (behavioral change). As such, trendy cyber-enabled affect operations symbolize a continuation of worldwide competitors wanting armed battle. Versus offensive cyber operations which may hack networked techniques, shut down a pipeline or interrupt communications, they concentrate on “hacking” human minds. That is available in notably helpful when a international energy desires to meddle in another person’s home politics.
CEIOs function by establishing self-sustaining loops of data that may manipulate public opinion and gas polarization. They’re “a brand new type of “divide and conquer” utilized to geopolitical situation of competitors relatively than in warfare,” I not too long ago argued with a co-author within the Intelligence and Nationwide Safety journal.
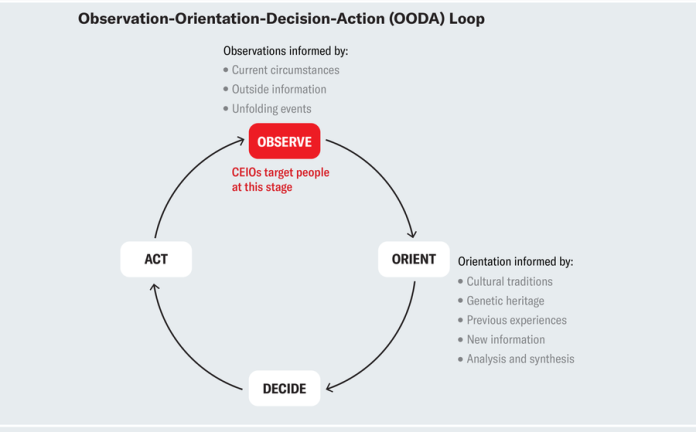
However how do these operations work? With a view to perceive that, we are able to use the navy idea of the observation-orientation-decision-action (OODA) loop, which is extensively utilized in planning technique and techniques. The mannequin helps clarify how people arrive at selections related to day by day life: people in a society (us) take info from the environment (remark) and make strategic decisions in consequence. Within the case of a dogfight (close-range aerial battle), the strategic selection would result in pilot’s survival (and navy victory). In day-to-day life, a strategic selection could be choosing the political chief that might finest symbolize our personal pursuits. Right here, altering what’s being noticed by injecting further info into the remark a part of the OODA loop can have vital repercussions. CEIOs purpose to do exactly that, by feeding totally different elements of the general public with focused messages on the remark stage aimed to in the end change their actions.
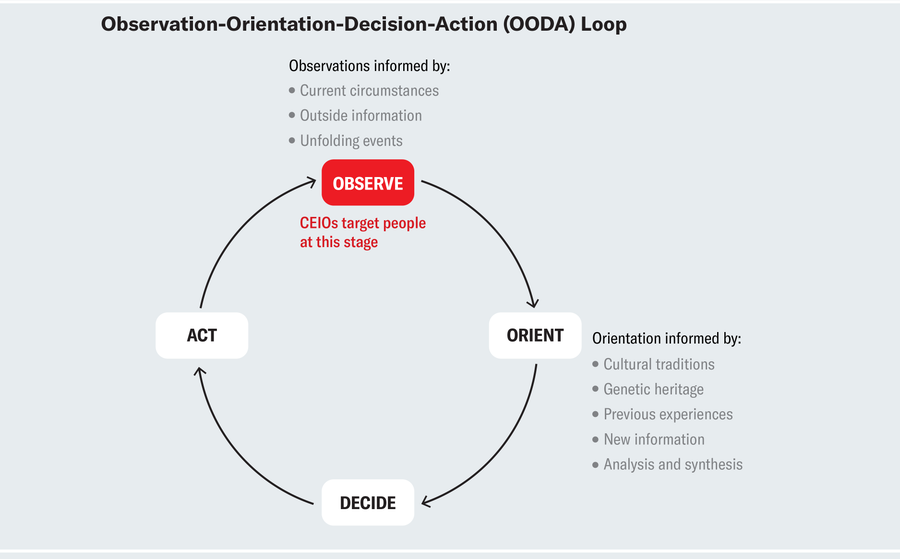
Amanda Montañez; Supply: A Discourse on Successful and Shedding, by John R. Boyd; Air College Press, 2018
So how do CEIOs interrupt the OODA loop utilizing social media? Cyber-enabled affect operations operate on widespread rules that may be understood via an identification-imitation-amplification framework. First, “outsiders” (malicious actors) establish goal audiences and divisive points via social media microtargeting.
Following this, the “outsiders” might pose as members of the audience by assuming false identities, via imitation which will increase their credibility. An instance is the 2016 Russian CEIO on Fb, which purchased advertisements to focus on U.S. audiences, manned by the notorious “troll factories” in St. Petersburg. In these advertisements, trolls assumed false identities and used the language that steered that they belonged to the focused society. Then they attempt to obtain affect via messages designed to resonate with goal audiences, selling a way of in-group belonging (on the expense of any bigger assumed group, such because the nation). Such messages might take the type of conventional disinformation, however may make use of factually right info. For that reason, utilizing the time period CEIO, as a substitute of “disinformation,” “misinformation” or “pretend information,” would possibly present extra analytical precision.
Lastly, tailor-made messages are amplified, each in content material (rising and diversifying the variety of messages) and by rising the variety of goal teams. Amplification may also happen through cross-platform posting.
Think about an instance: a submit by a not too long ago enlisted soldier who recounts their lived expertise of seeing September eleventh on TV and says that it was this occasion that motivated them to hitch the navy. It is a submit that was shared by the Veterans Throughout the Nation Fb web page. The content material of this submit could also be solely fabricated, and VAN might not exist “in actual life.” Nevertheless, such a submit, whereas fictional, can have the emotive affect of authenticity, notably in how it’s visually introduced on a digital media platform. And it may be leveraged for functions apart from selling a shared sense of patriotism, relying on to what content material it turns into linked and amplified via.
In its CEIO utilizing Fb, the Russian Web Analysis Company focused various home audiences within the U.S. via particularly crafted messaging aimed toward interfering within the 2016 election, as recounted in the Mueller Report.Reportedly, 126 million People had been uncovered to Russian efforts to affect their views, and their votes, on Fb. Totally different audiences heard totally different messages, with teams recognized utilizing Fb’s menu-style microtargeting options. Proof exhibits that nearly all of Russian-bought advertisements on Fb focused African People with messages that didn’t essentially comprise false info, however relatively centered on subjects together with race, justice and police. Past the U.S., Russia reportedly focused Germany, in addition to the U.Okay.
To successfully make strategic selections, people should accurately observe their environments. If the noticed actuality is filtered via a manipulated lens of divisiveness, manageable factors of social disagreement (anticipated in wholesome democracies) might be changed into probably unmanageable divisions. For instance, the favored emphasis on polarization within the U.S. ignores the truth that most individuals are usually not as politically polarized as they suppose. Belief in establishments might be undermined, even with out the assistance of “pretend information.”
Because the identification-imitation-amplification framework highlights, the query of who can legitimately take part in debates and search to affect public opinion is of essential significance and has a bearing on what’s the “actuality” that’s being noticed. When expertise permits outsiders (international malicious actors) to credibly pose as professional members of a sure society, the potential dangers of manipulation improve.
With about 49 % of the worldwide inhabitants collaborating in elections in 2024, we should counter CEIOs and election interference. Understanding imitation, identification and amplification is simply the place to begin. International affect operations will make the most of truthful info to sway public opinion. We should suppose deeply about what which means for home political affairs. Moreover, if our on-line world offers entry and anonymity facilitating affect operations aimed toward swaying audiences and affecting elections, democracies should successfully restrict that entry to genuine, professional customers whereas staying true to rules of free speech. This a tough job, one we urgently have to undertake.
That is an opinion and evaluation article, and the views expressed by the creator or authors are usually not essentially these of Scientific American.






























![[2405.08825] Thermodynamic restrict in studying interval three](https://i0.wp.com/arxiv.org/static/browse/0.3.4/images/arxiv-logo-fb.png?w=218&resize=218,150&ssl=1)